Overview
Webhooks allow you to receive real-time notifications when events occur in GameBoost, such as when customers purchase orders or when reports are issued. Instead of polling the API for updates, webhooks push notifications directly to your application.Webhooks reduce API calls dramatically and provide near-instant updates, making them essential for responsive integrations.
Benefits of Webhooks
Real-time Updates
Receive instant notifications when events occur, keeping your application in sync
Reduced API Calls
Eliminate the need for polling, dramatically reducing your API usage
Better User Experience
Provide immediate feedback to your users about status changes
Reliable Delivery
Automatic retries ensure you don’t miss critical events
Setting Up Webhooks
Configure webhooks directly from your Partner Dashboard:Navigate to Webhooks Settings
Log in to the Partner Dashboard and go to Settings → Developers → Webhooks.

Add a New Webhook Endpoint
Click New Webhook to create a new webhook configuration.You’ll need to provide: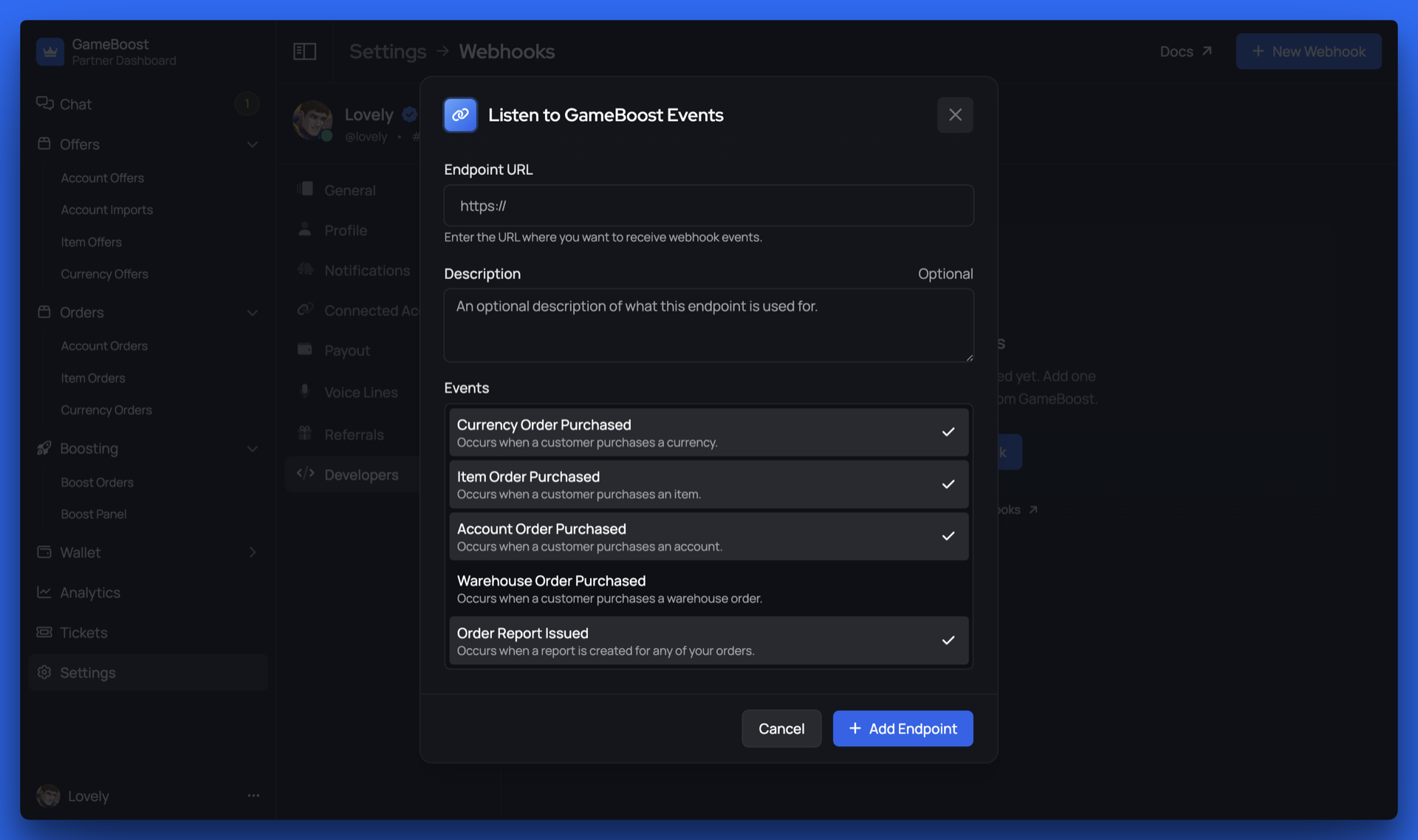
- Endpoint URL: The HTTPS URL where you want to receive webhook events
- Description: A friendly name to identify this webhook
- Events: Select which events you want to receive

Configure Authentication
Copy the secret key to verify webhook authenticity. GameBoost will include this in the webhook signature, allowing you to verify the webhook came from us.
We strongly recommend using webhook signatures to prevent unauthorized webhook calls to your endpoint.
Webhook Payload Structure
All webhook events follow a consistent structure:Payload Fields
The type of event that occurred (e.g.,
currency.order.purchased, order.report.issued)The event data containing the resource that triggered the webhook. Fields vary based on the event type.
Available Webhook Events
GameBoost sends webhooks for various events in your seller account. See the complete list of webhook events and their payloads:View All Webhook Events
Explore detailed documentation for each webhook event type
Webhook Signatures
All webhooks include aSignature header containing an HMAC SHA-256 signature. You should verify this signature to ensure the webhook came from GameBoost.
Signature Verification
The signature is computed as follows:Webhook Retries
GameBoost automatically retries failed webhook deliveries to ensure reliable event delivery using an exponential backoff strategy.Retry Strategy
| Attempt | Wait Time | Description |
|---|---|---|
| 1 | Immediate | Initial delivery attempt |
| 2 | ~10 seconds | First retry |
| 3 | ~100 seconds | Second retry (final attempt) |
After 3 failed attempts, the webhook will be marked as failed and no further retries will be attempted for that event.
Successful Delivery Criteria
A webhook is considered successfully delivered if your endpoint:- Responds within 3 seconds
- Returns a
2xxstatus code (200-299)
Handling Retries
Implement idempotency to ensure webhook events are only processed once, even if they’re retried:Best Practices
Return 200 quickly
Return 200 quickly
Process webhooks asynchronously and return a 200 status code immediately. Don’t wait for database operations or external API calls to complete.
Implement idempotency
Implement idempotency
Store processed webhook identifiers and skip events you’ve already processed. This prevents duplicate processing if a webhook is retried.
Verify signatures
Verify signatures
Always verify the
Signature header to ensure webhooks are authentic.Log webhook events
Log webhook events
Log all incoming webhooks for debugging and auditing purposes.
Handle failures gracefully
Handle failures gracefully
If processing fails, log the error but still return 200 to prevent retries. You can reprocess failed events later from your logs.
Test thoroughly
Test thoroughly
Use the test webhook feature in the Partner Dashboard to verify your endpoint works correctly before going live.
Using Hookdeck for Webhook Management
For production applications, we recommend using Hookdeck to manage your webhooks reliably.Hookdeck
Hookdeck provides webhook infrastructure with automatic retries, monitoring, and debugging
Troubleshooting
Webhooks not being received
Webhooks not being received
Possible causes:
- Your endpoint is not accessible from the internet
- Firewall or security group blocking requests
- Incorrect endpoint URL configured
- Server not responding within 3 seconds
- Verify your endpoint URL is correct and accessible
- Check firewall rules and allowlist GameBoost User-Agent
- Test with the “Send Test Event” button
- Ensure your endpoint returns 200 quickly
Receiving duplicate webhooks
Receiving duplicate webhooks
Cause: Your endpoint is not returning 200 quickly enough, causing GameBoost to retrySolution: Implement async processing and return 200 immediately
Signature verification failing
Signature verification failing
Possible causes:
- Using wrong webhook secret
- Modifying payload before verification
- Character encoding issues
- Verify you’re using the correct secret from Partner Dashboard
- Verify signature before parsing or modifying the payload
- Use the raw request body for verification
High failure rate
High failure rate
Check:
- Server logs for errors
- Response times (should be < 3 seconds)
- Server capacity and resource usage
- Database connection issues
Webhook Security
Security Checklist
- ✅ Use HTTPS only (HTTP endpoints are rejected)
- ✅ Verify webhook signatures on every request
- ✅ Store webhook secrets securely (environment variables, secrets manager)
- ✅ Validate event data before processing
- ✅ Implement rate limiting on your webhook endpoint
- ✅ Log suspicious webhook activity
- ✅ Rotate webhook secrets periodically